SECURE.SOVEREIGN.RESILIENT.
HOW DEFENSE WORKS
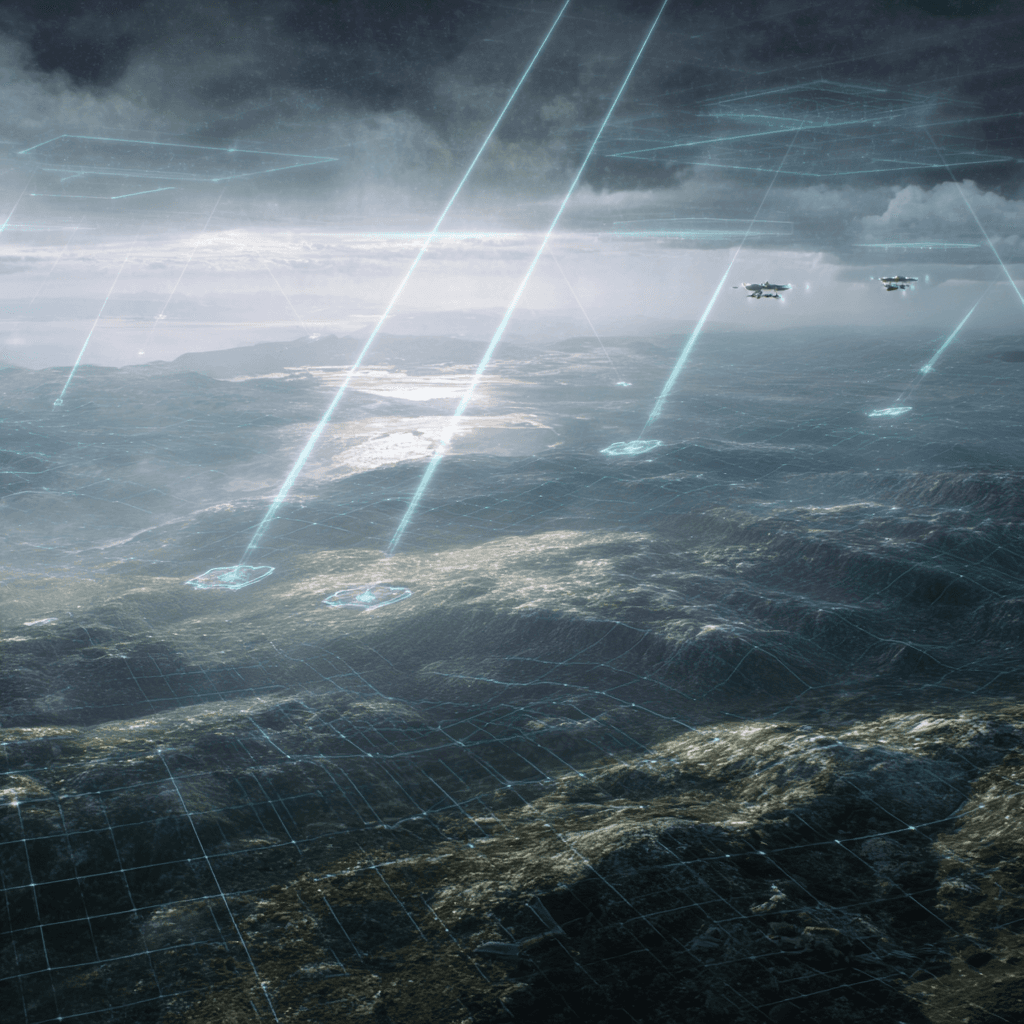
Local Detection
Sensors analyze threats in real-time on the edge. No data leaves the secure perimeter.
Federated Consensus
Nodes share threat signatures (not raw data) to form a collective defense intelligence.
Autonomous Response
The network reacts instantly to neutralize threats, isolating affected nodes automatically.
Resilient Mesh
Self-healing architecture ensures continuous operation even if individual nodes are compromised.
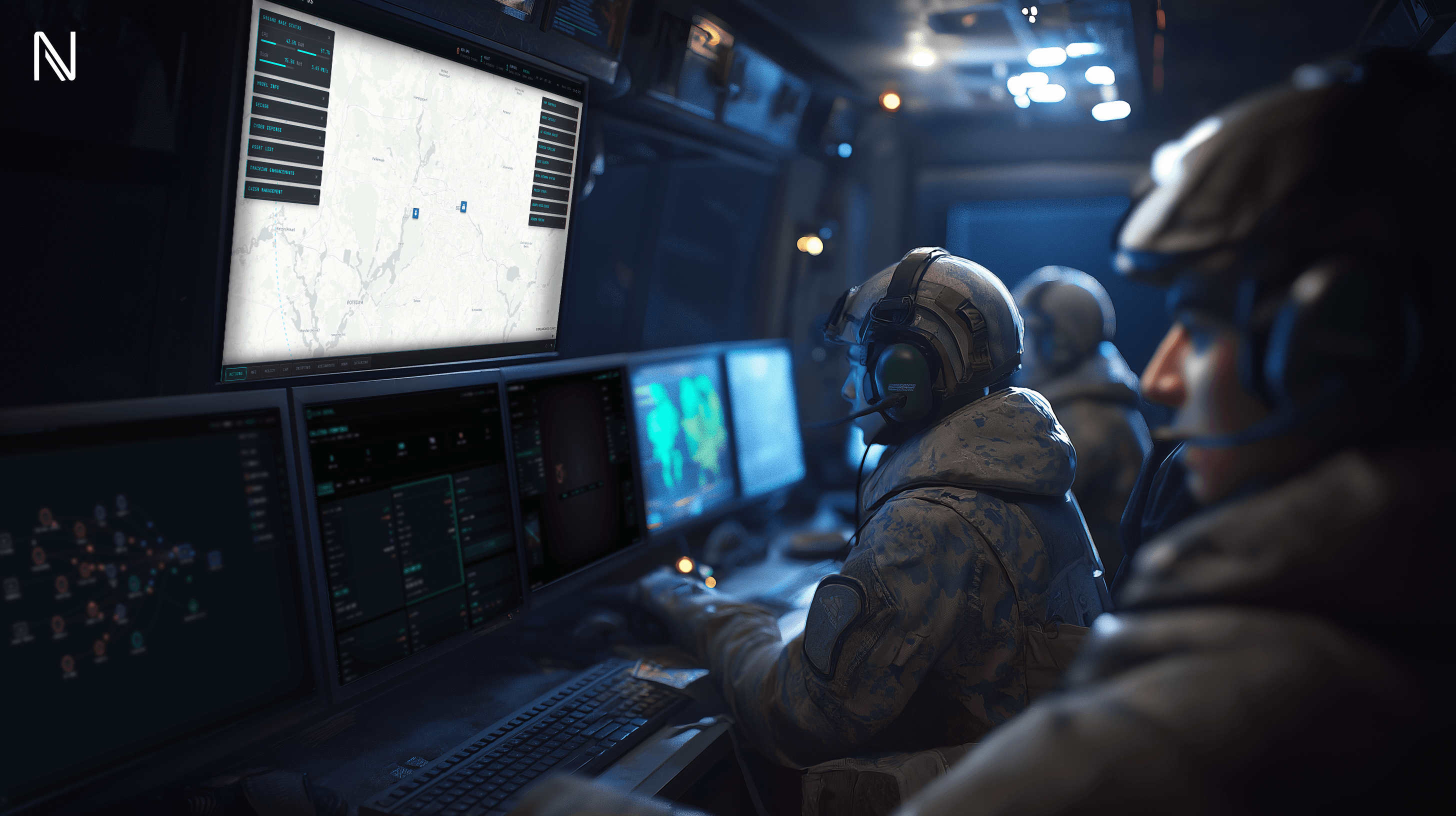
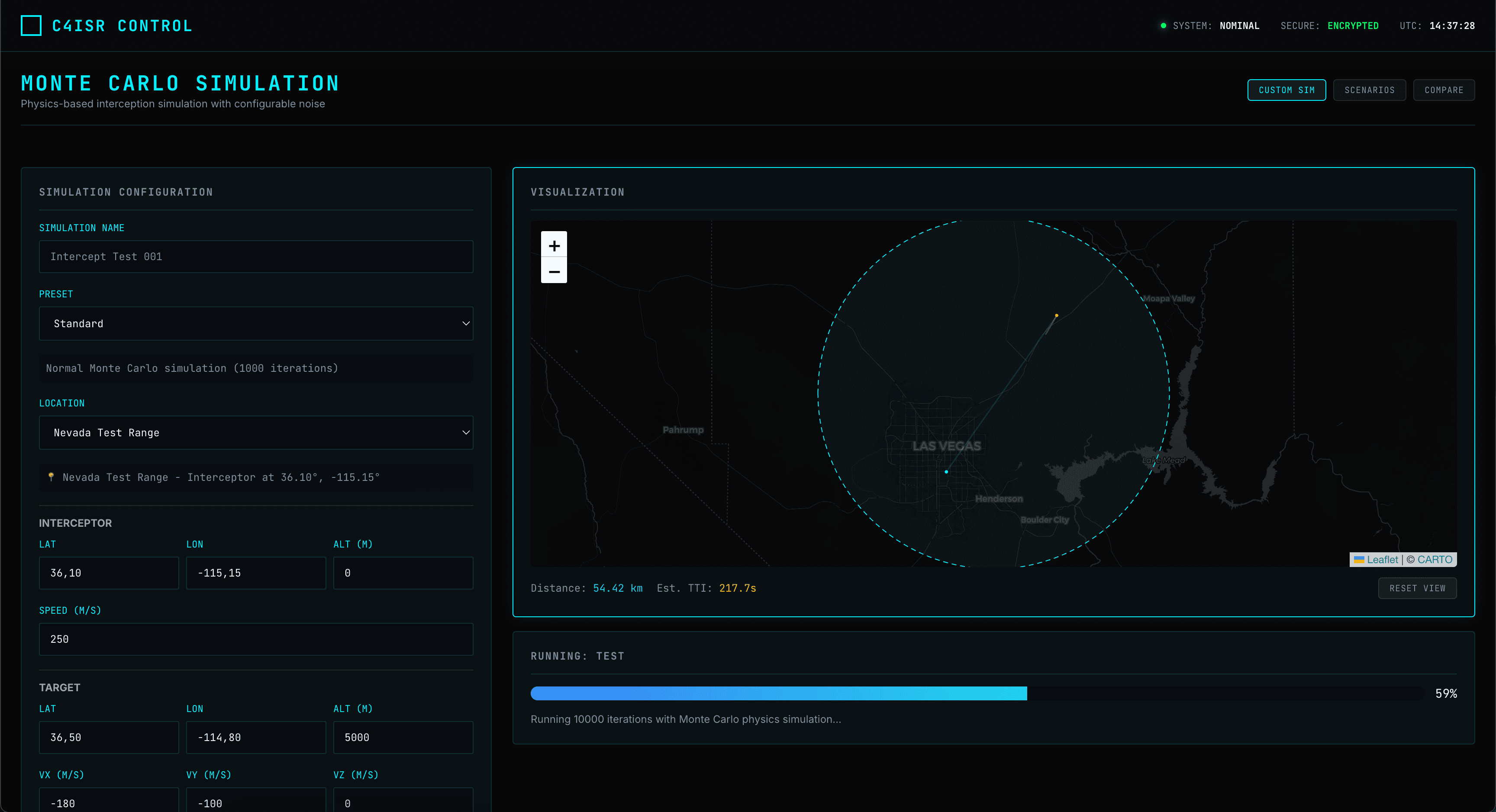
MISSION CONTROL
Tactical Command & Control
AXON OS provides the real-time tactical layer for modern defense operations. Gain situational awareness on a battlefield-grade interface.
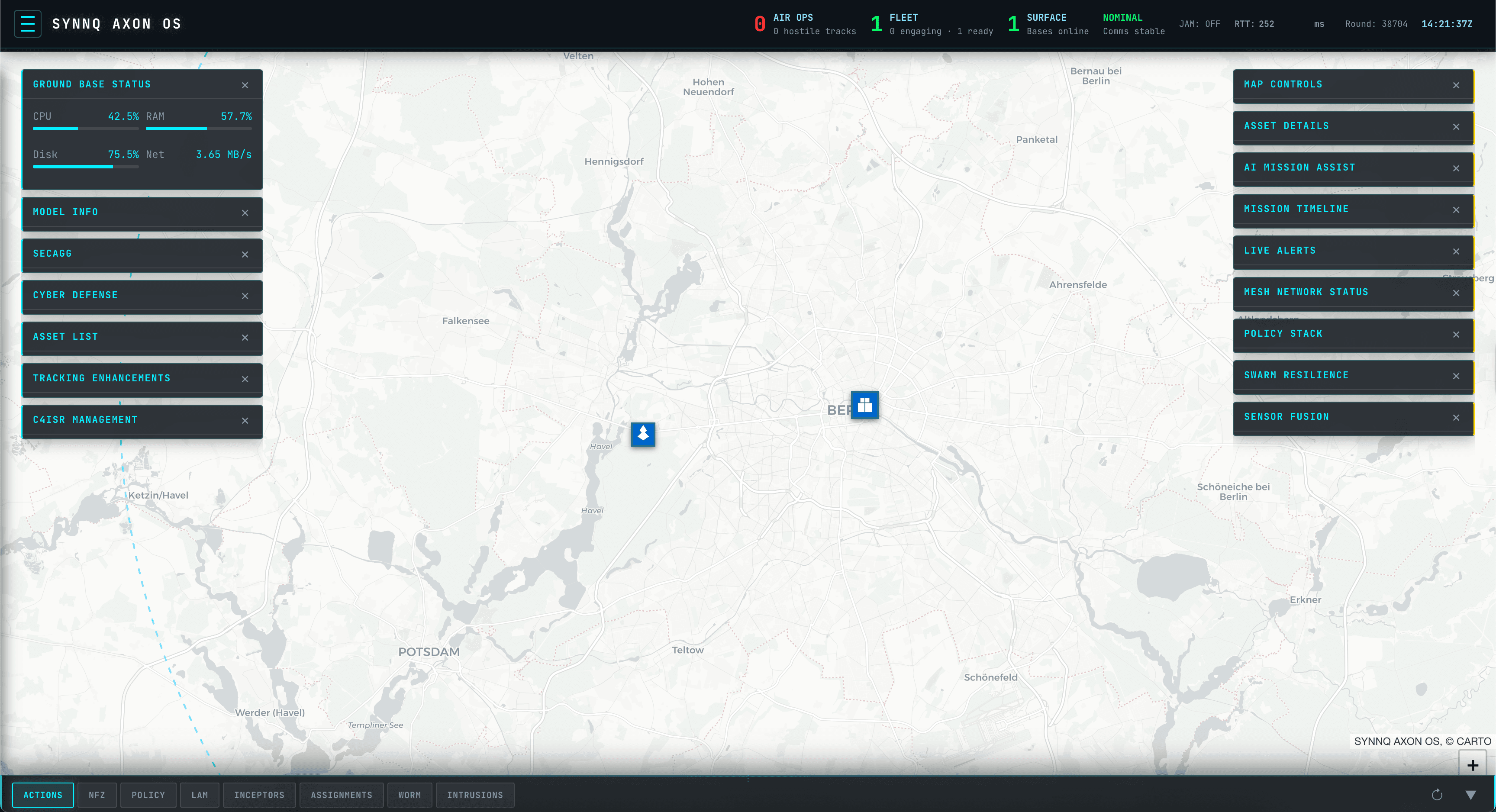
Tactical Dashboard
Live operational map, fleet status, and 1-click access to domain modules.
Ground Base Health
Monitor resources, and secure aggregation state under mission-critical load.
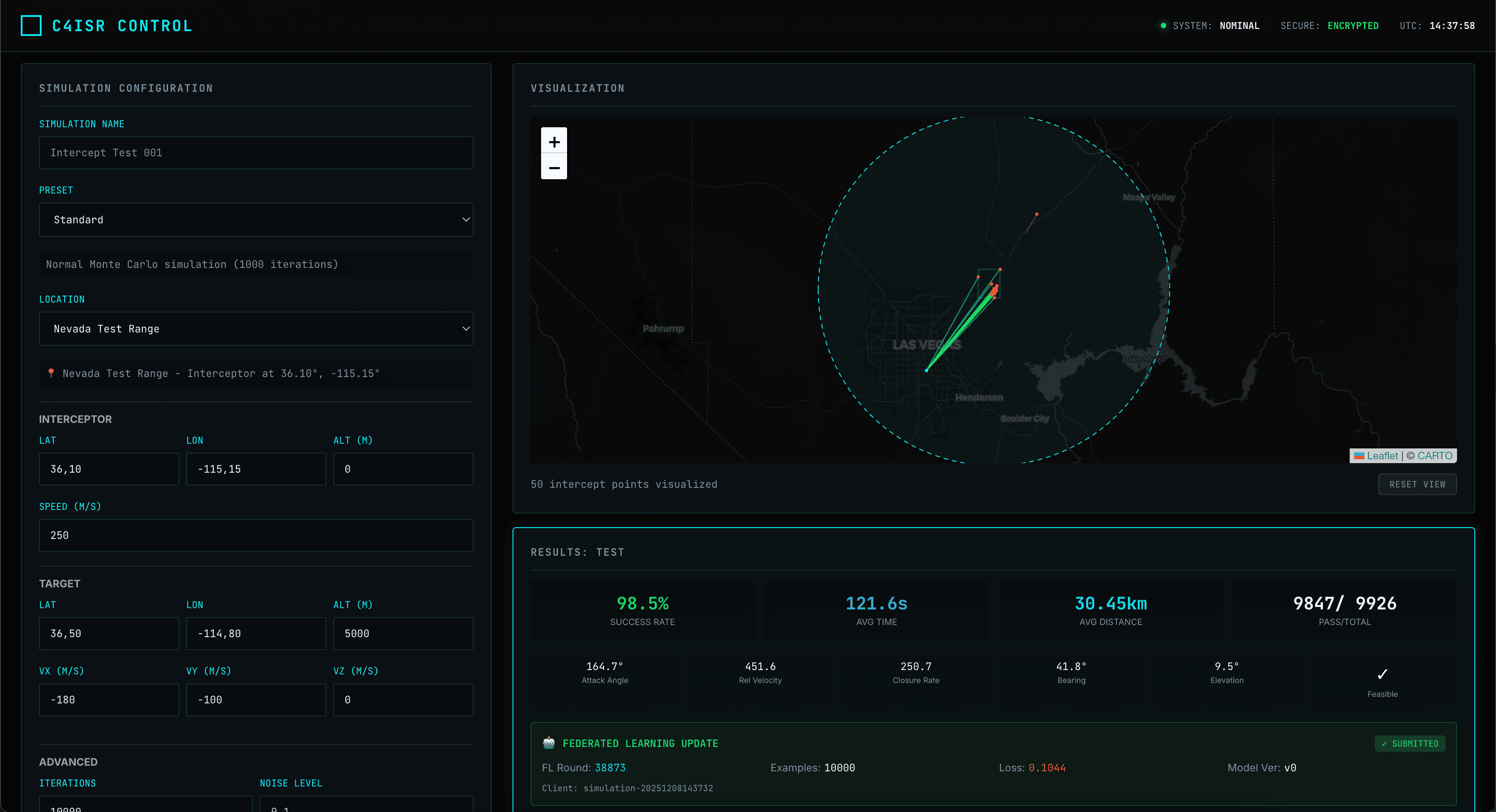
Operations Center
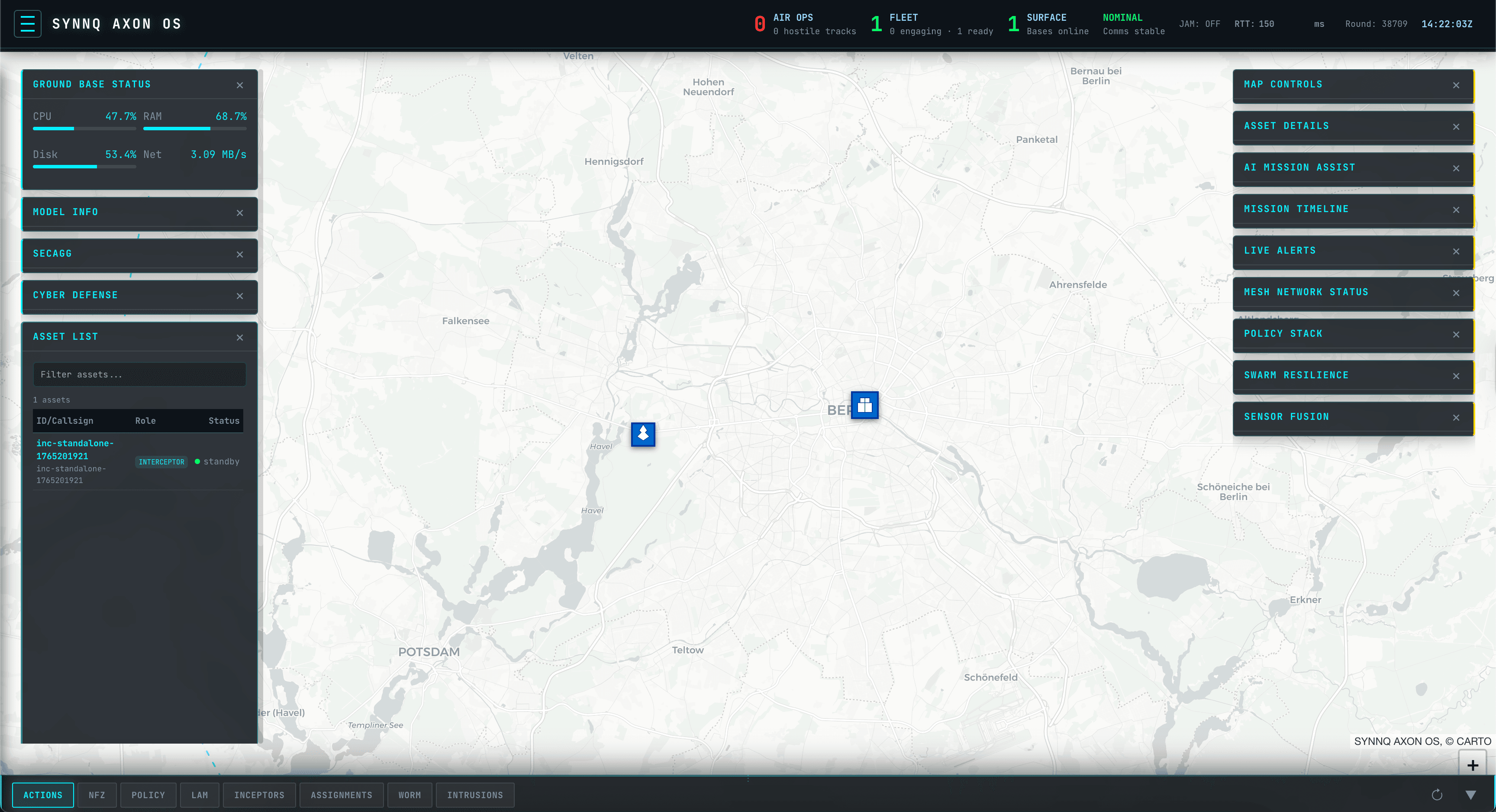
A centralized hub for mission planning, cyber defense, and asset management.
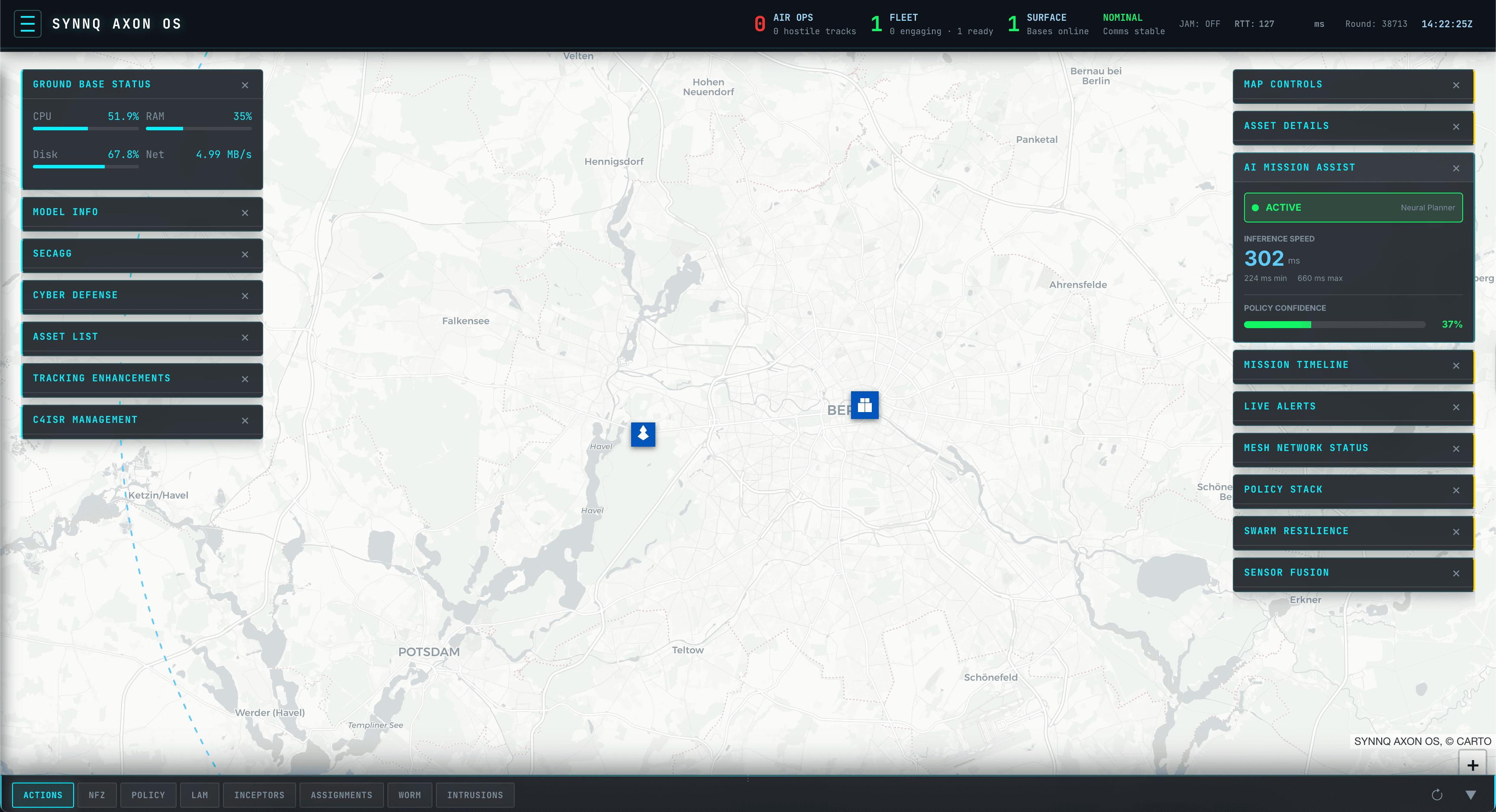
AI Mission Assist
Neural mission planning with <400ms inference and tactical reasoning.
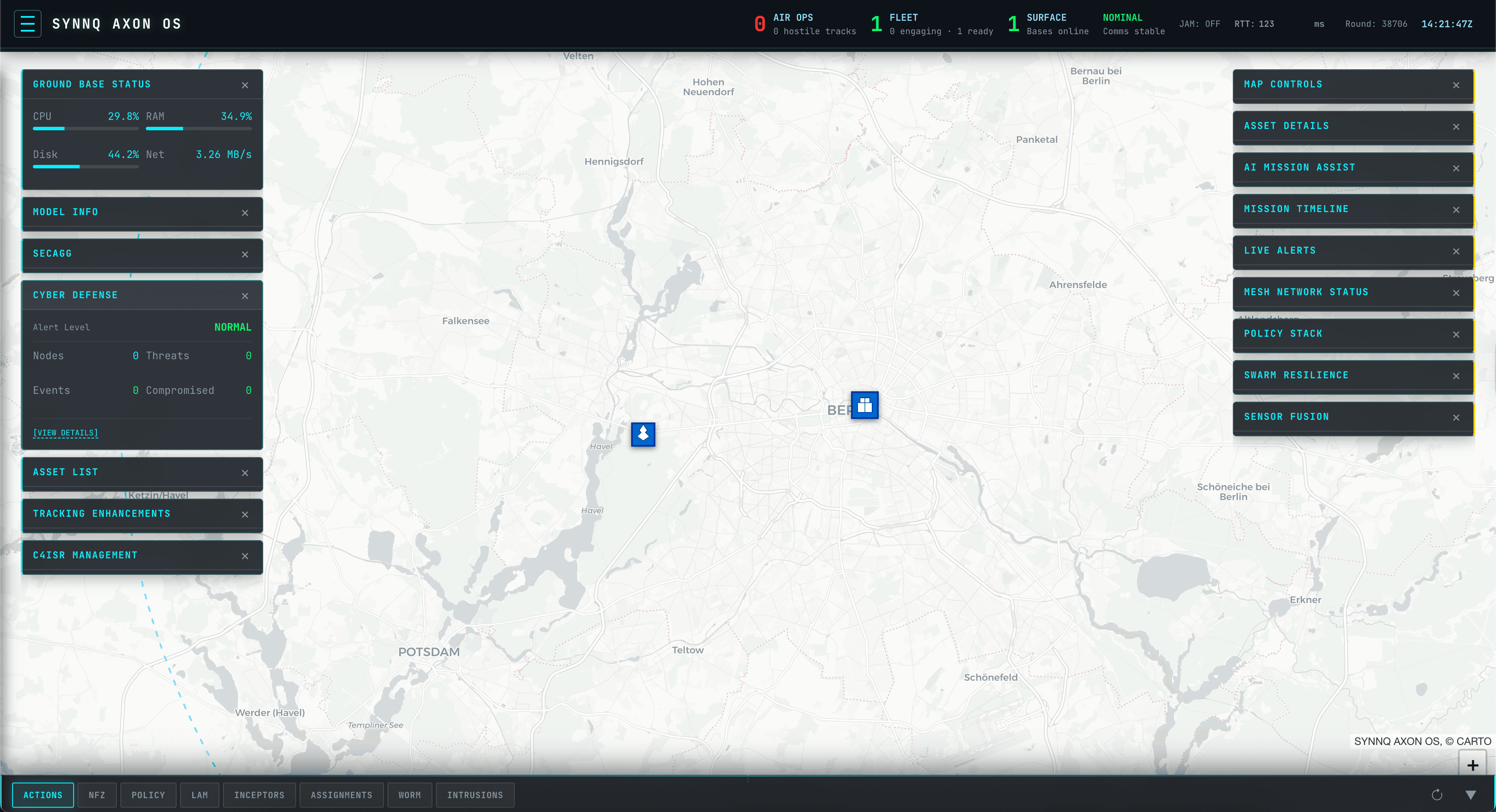
Cyber Defense Ops
Zero-trust monitoring and automated response workflows.
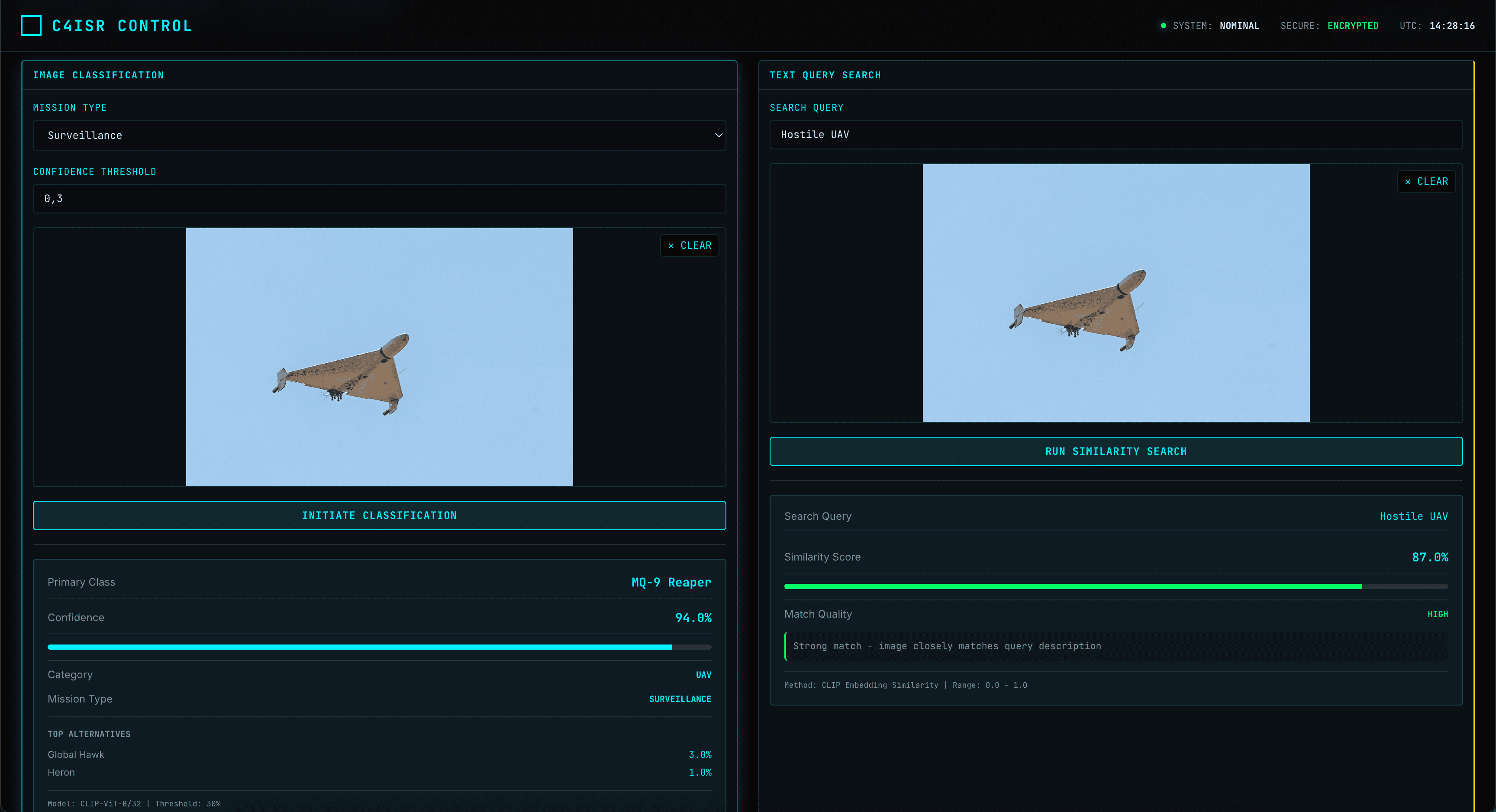
Sensor Fusion & ISR
Fused picture of the battlespace across all sensing modalities including EO/IR, ADS-B, and radar.
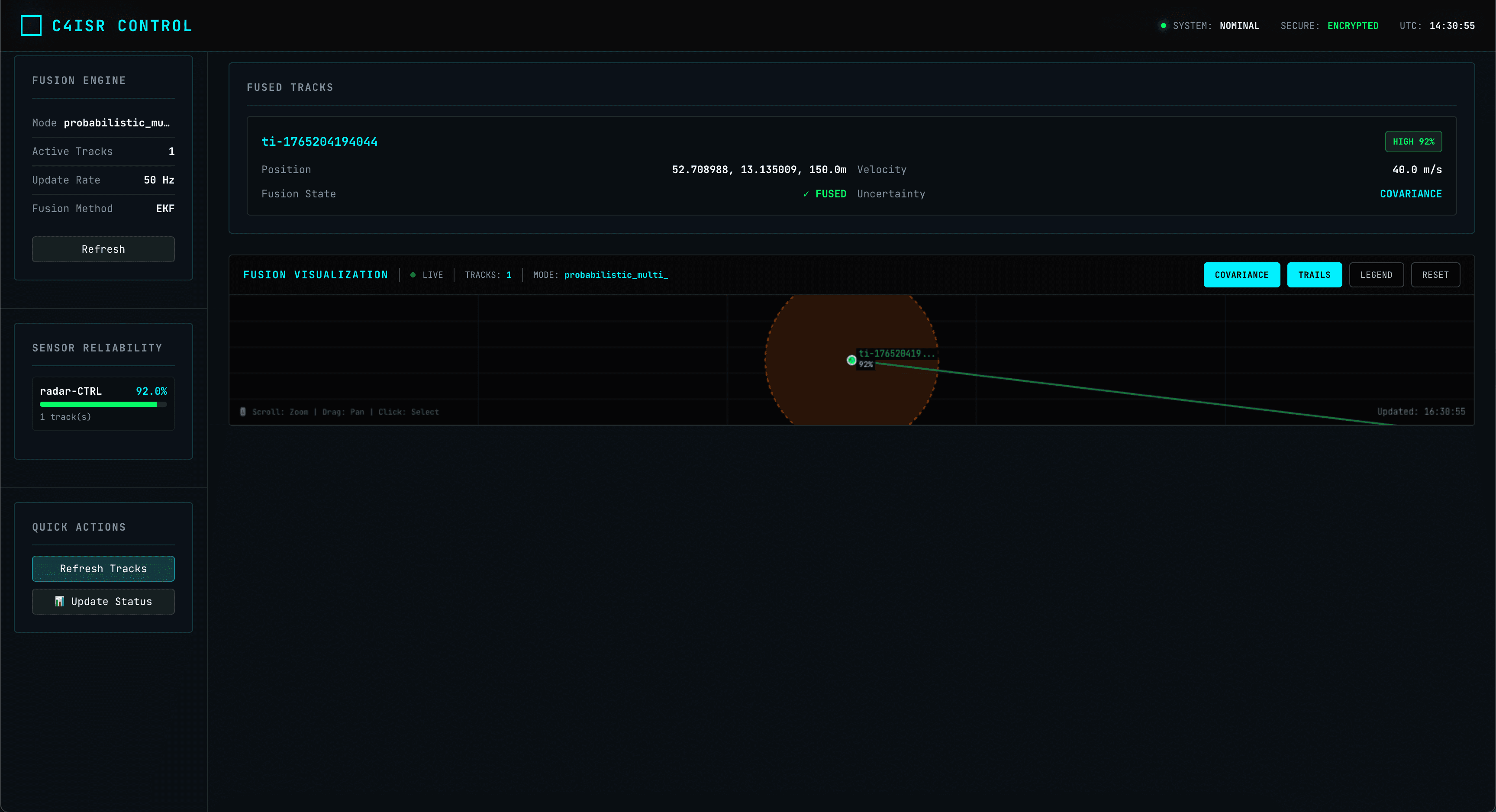
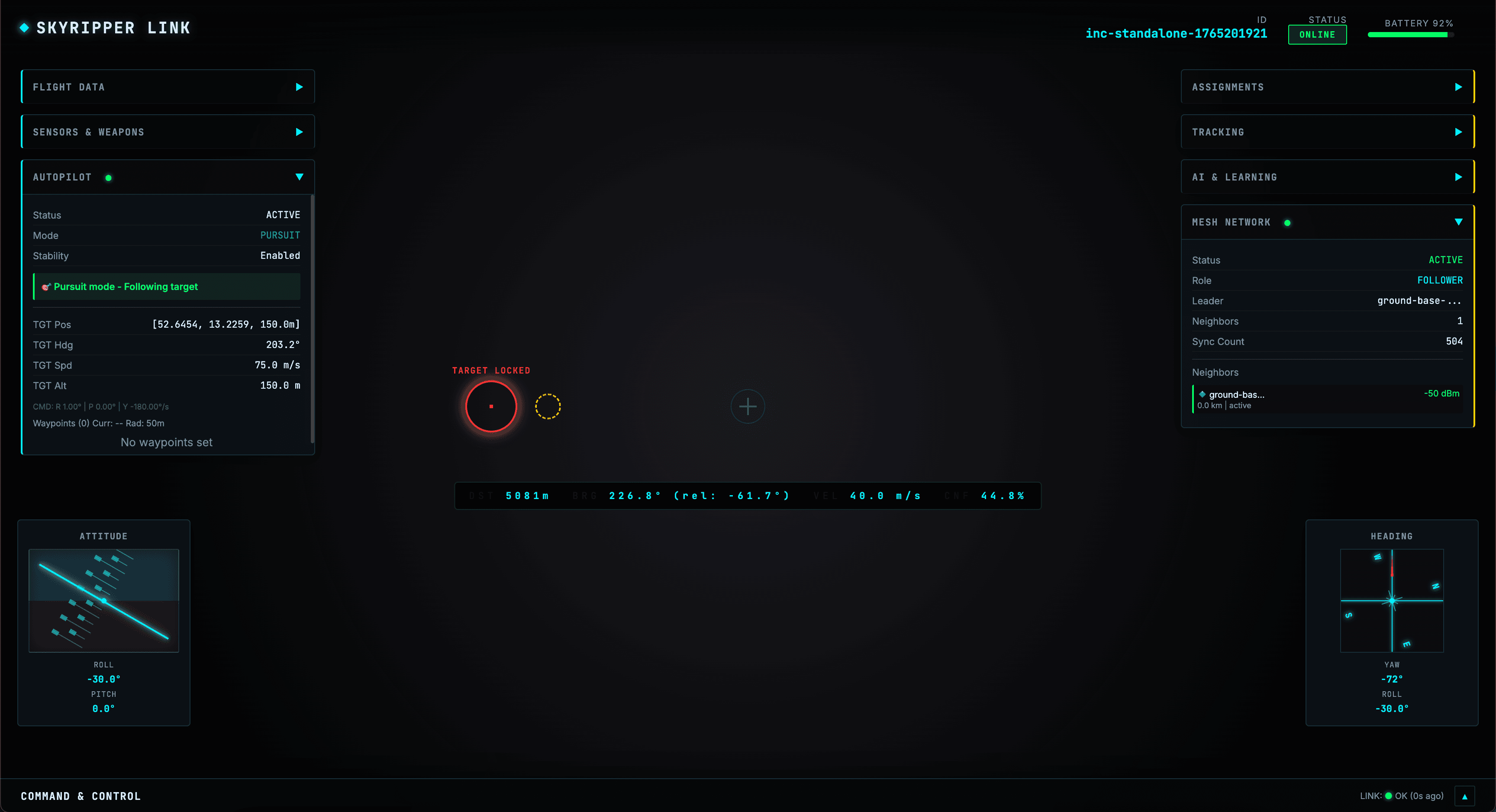
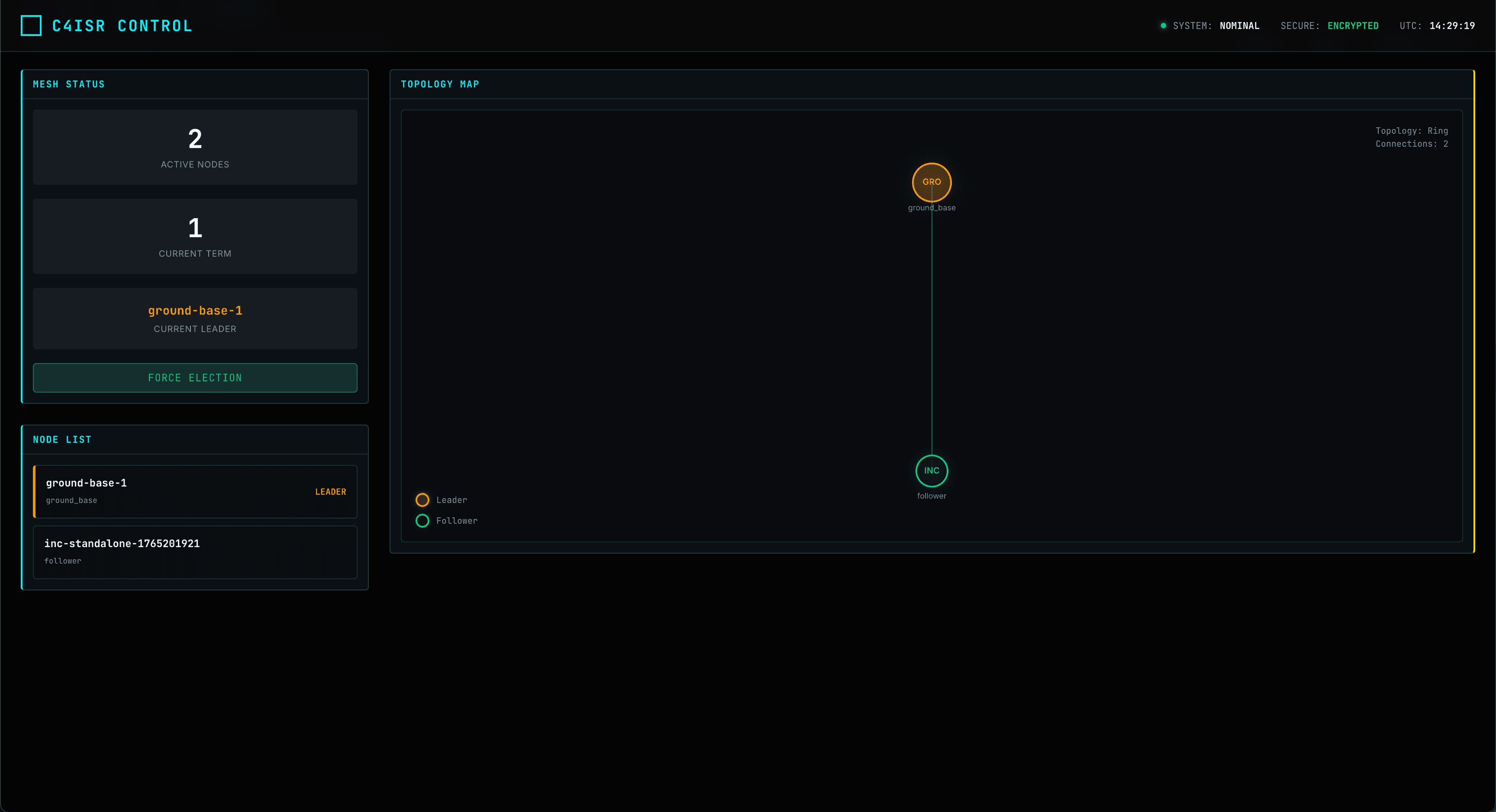
Mesh Network & Autonomy
Self-healing swarm fabric with Raft consensus. Resilient against node loss or comms jamming.
Distributed Consensus
Leader election and world model sync across 2–10+ nodes.
Encrypted Comms
Military-grade encryption for all inter-node coordination.
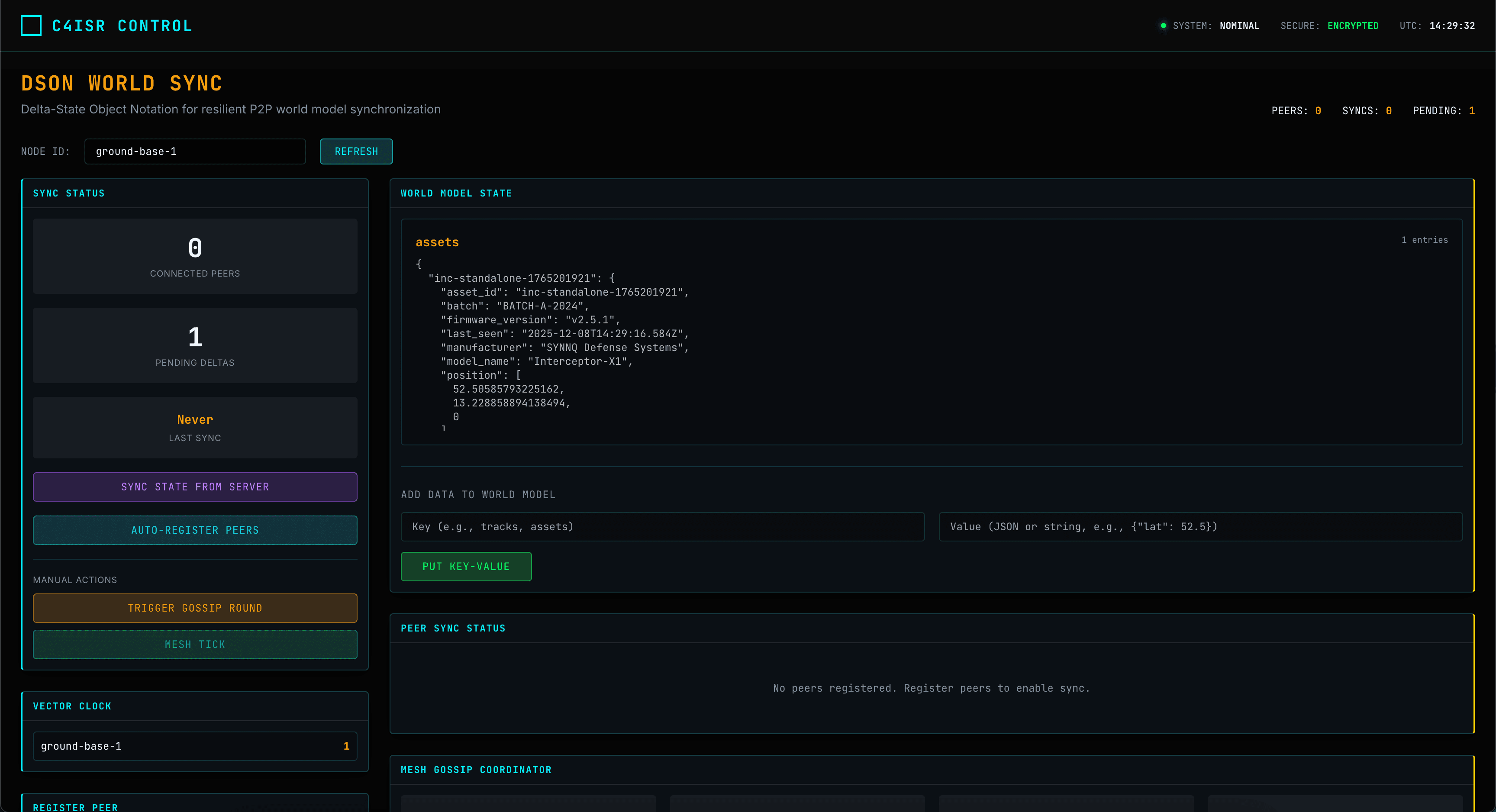
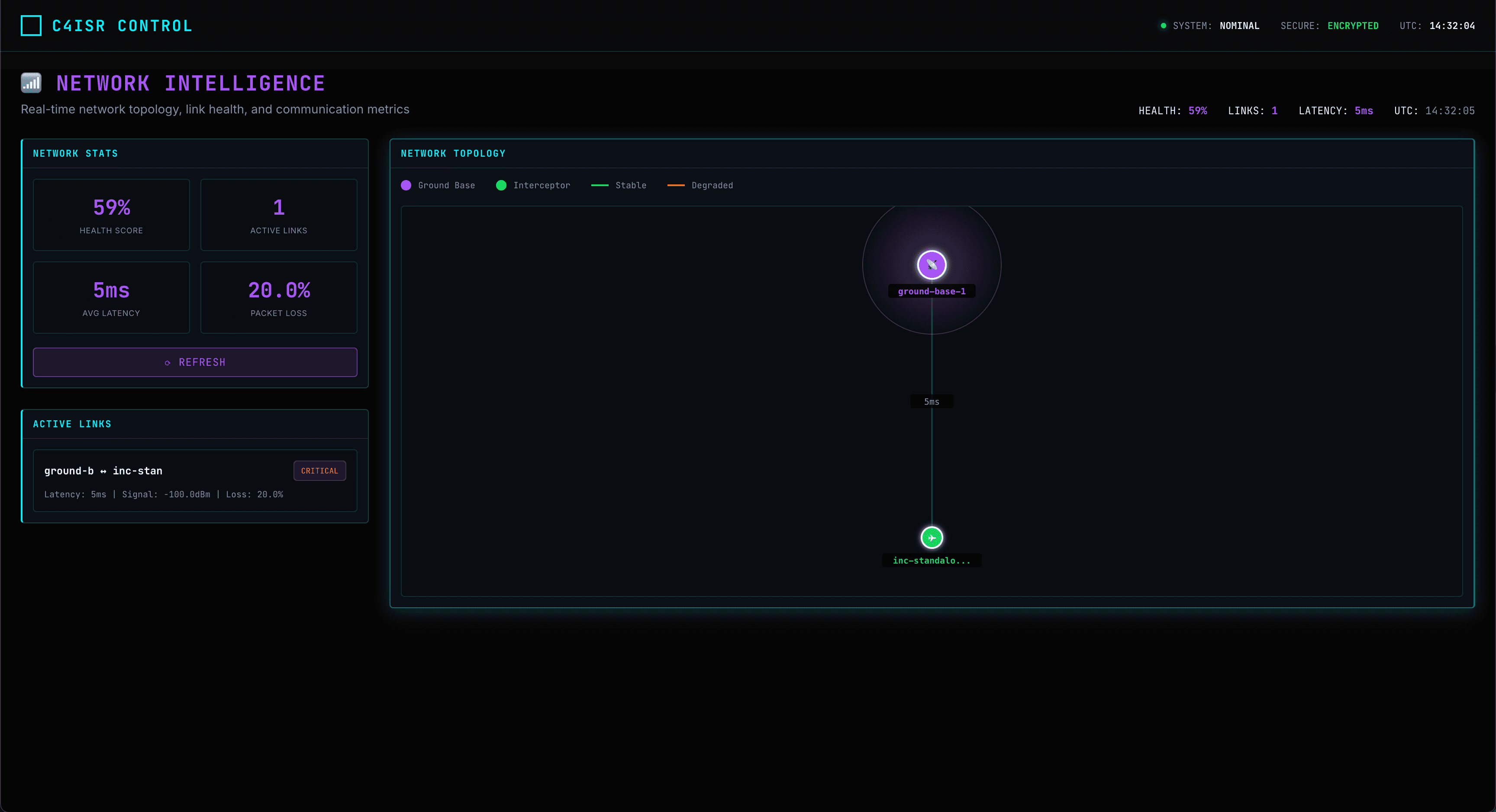
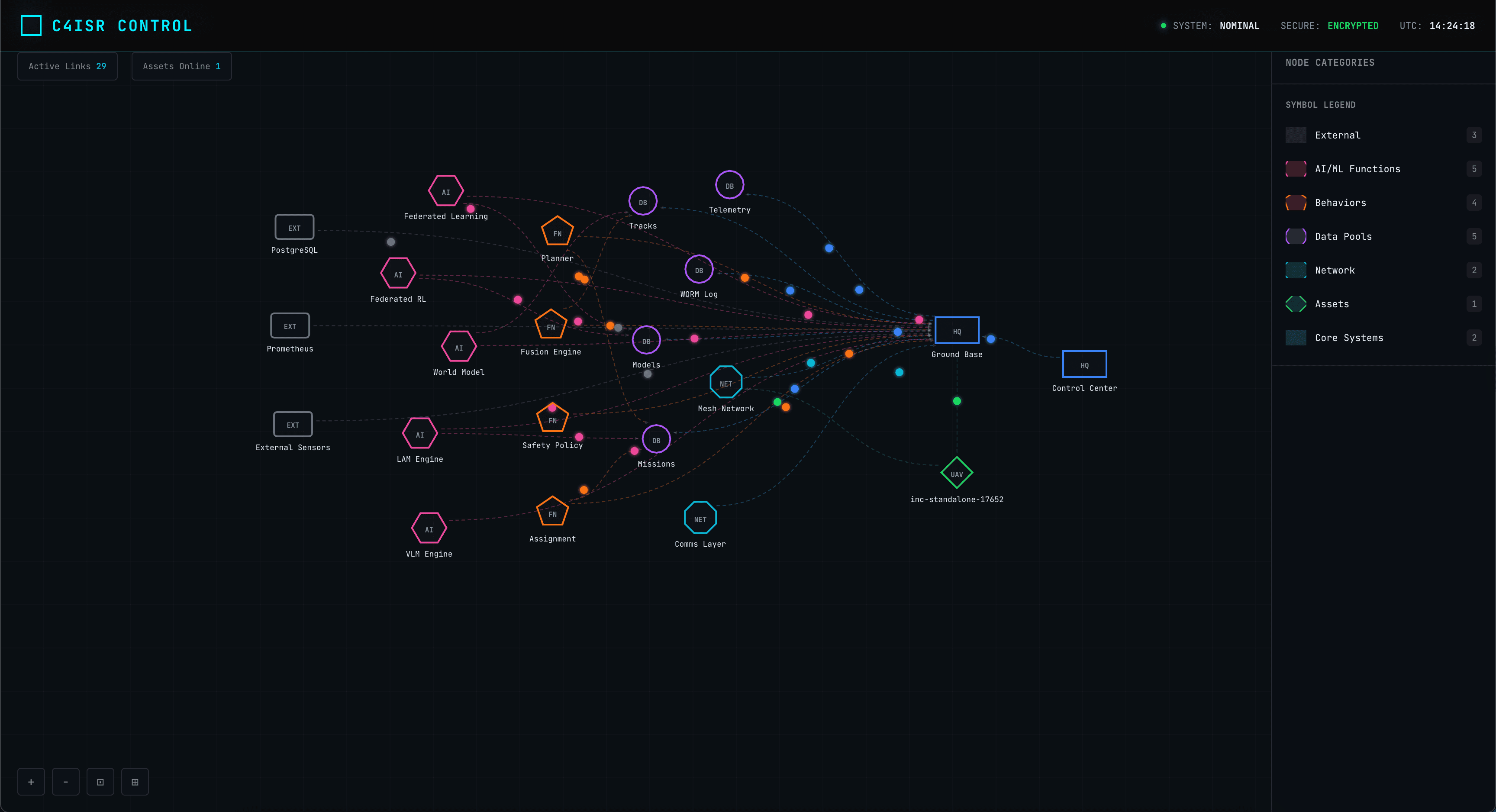
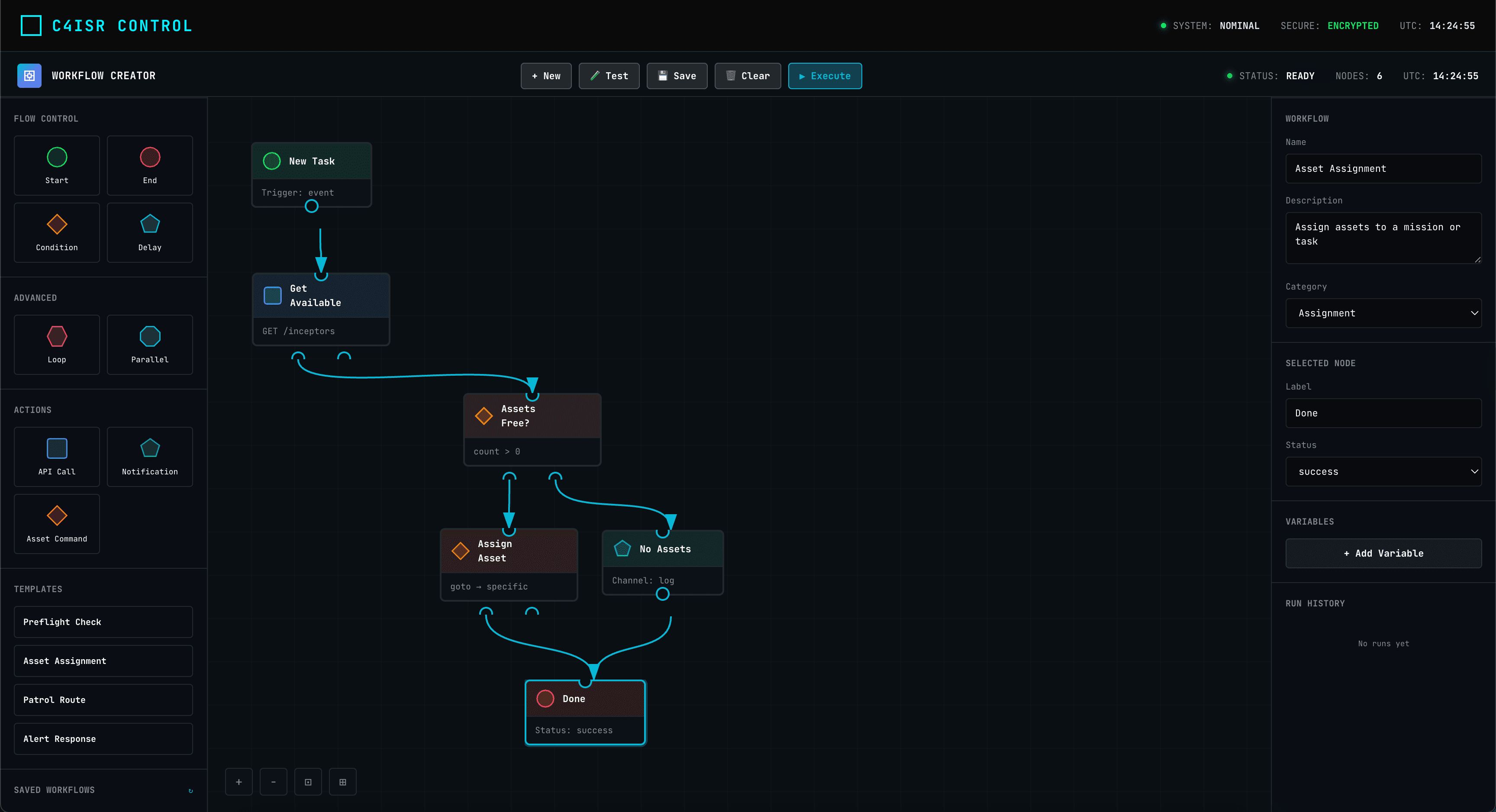
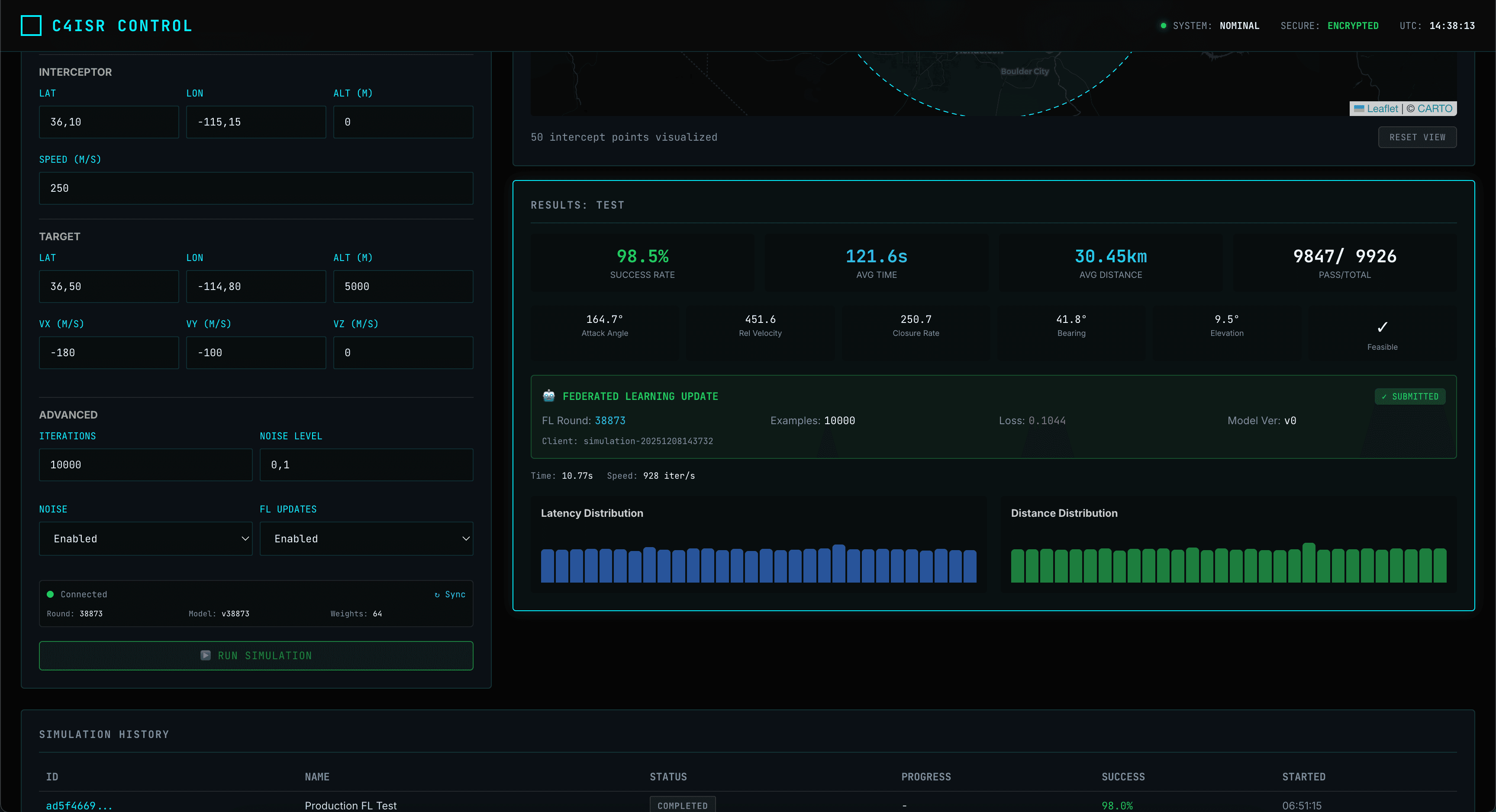
Architecture & Automation
Interactive graphs of all assets and no-code automation workflows.
System Explorer
Visual dependency mapping between AI models, sensors, and policies.
Flow Forge
Drag-and-drop mission automation with visual DAGs.
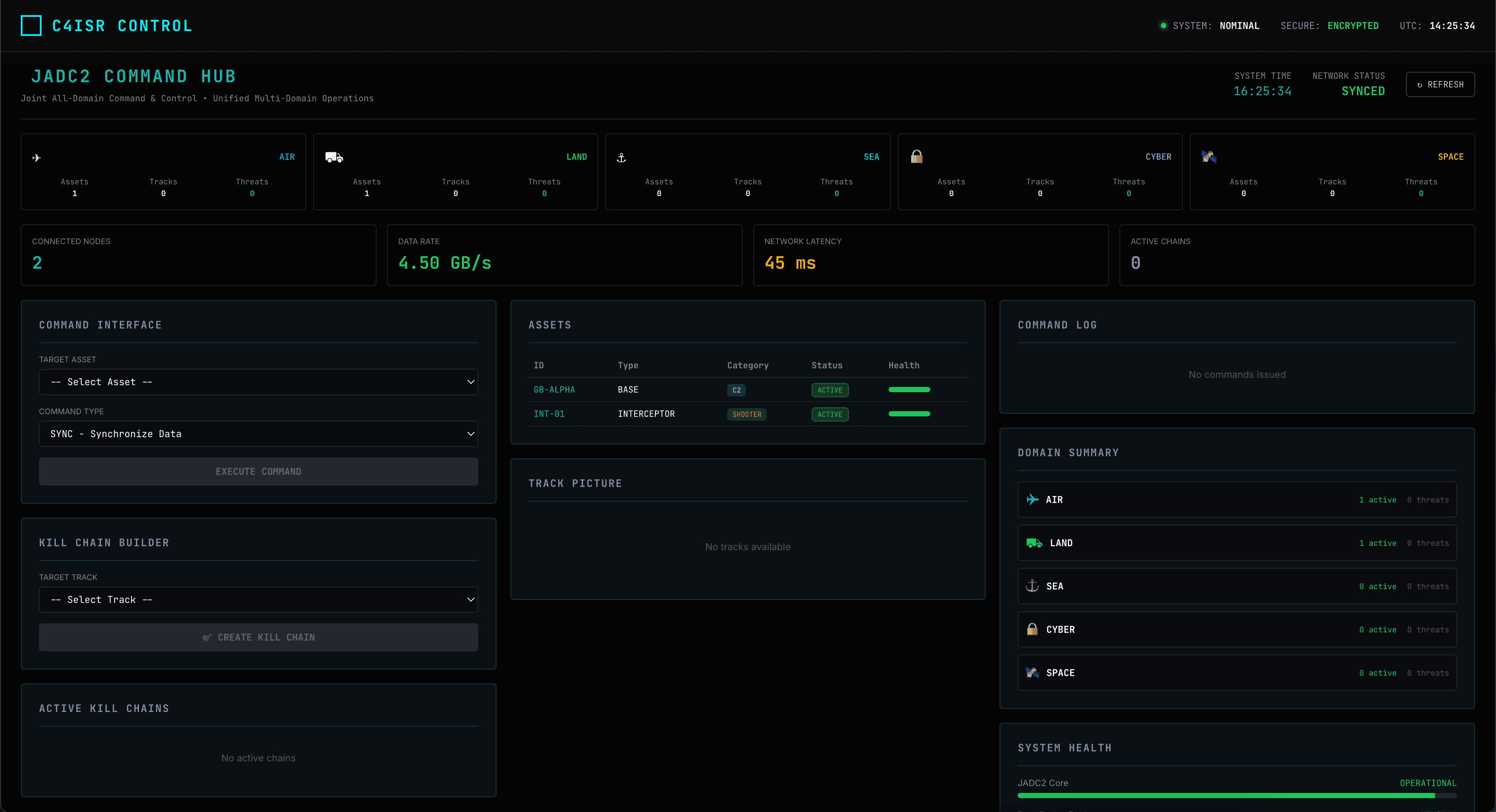
Global Interoperability
Interoperable with next-generation NATO and coalition workflows.
JADC2 Hub
Link-16 integration and coalition data sharing.
Swarm Autonomy
Distributed behavior policies for formation control.

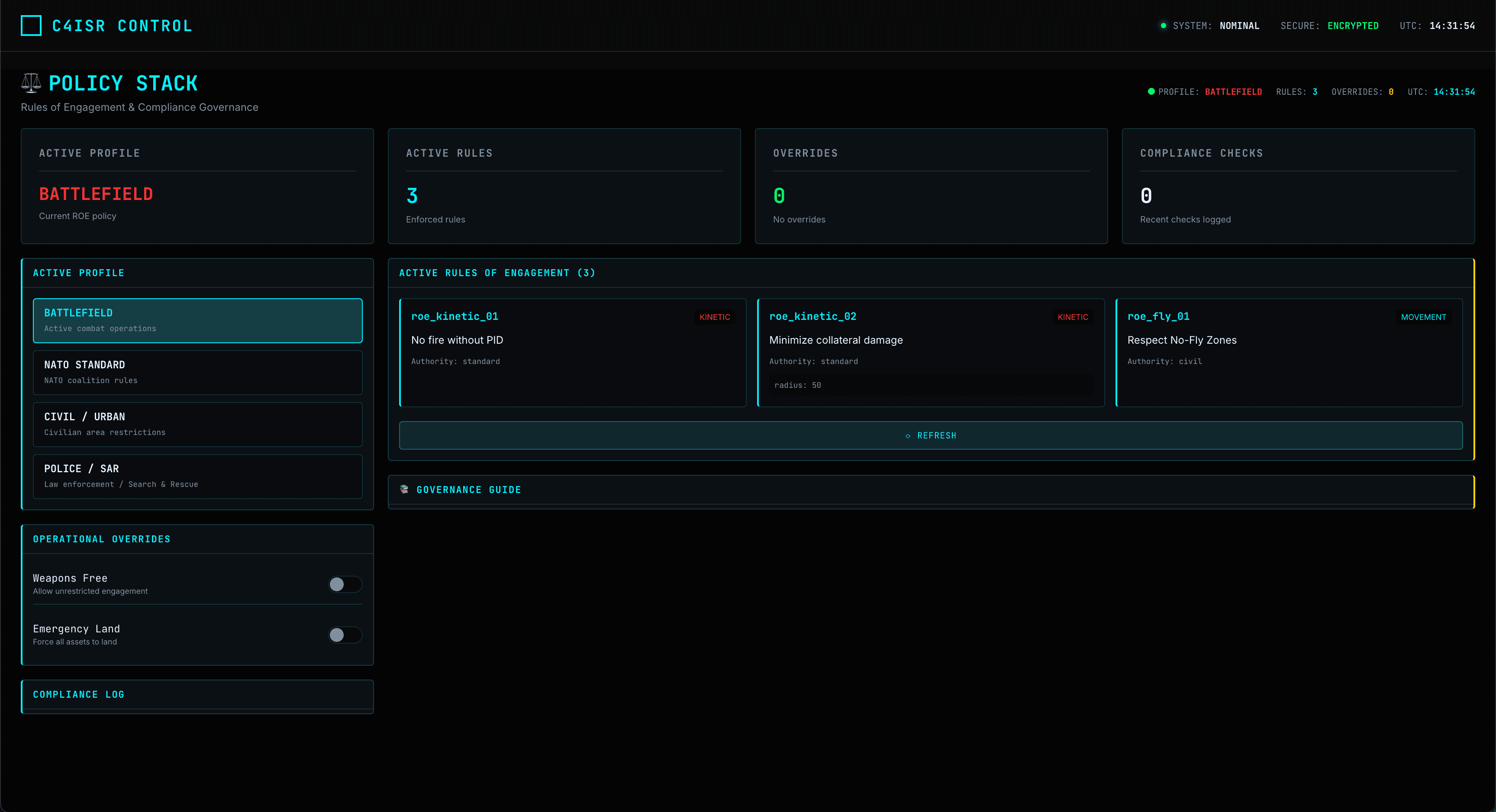
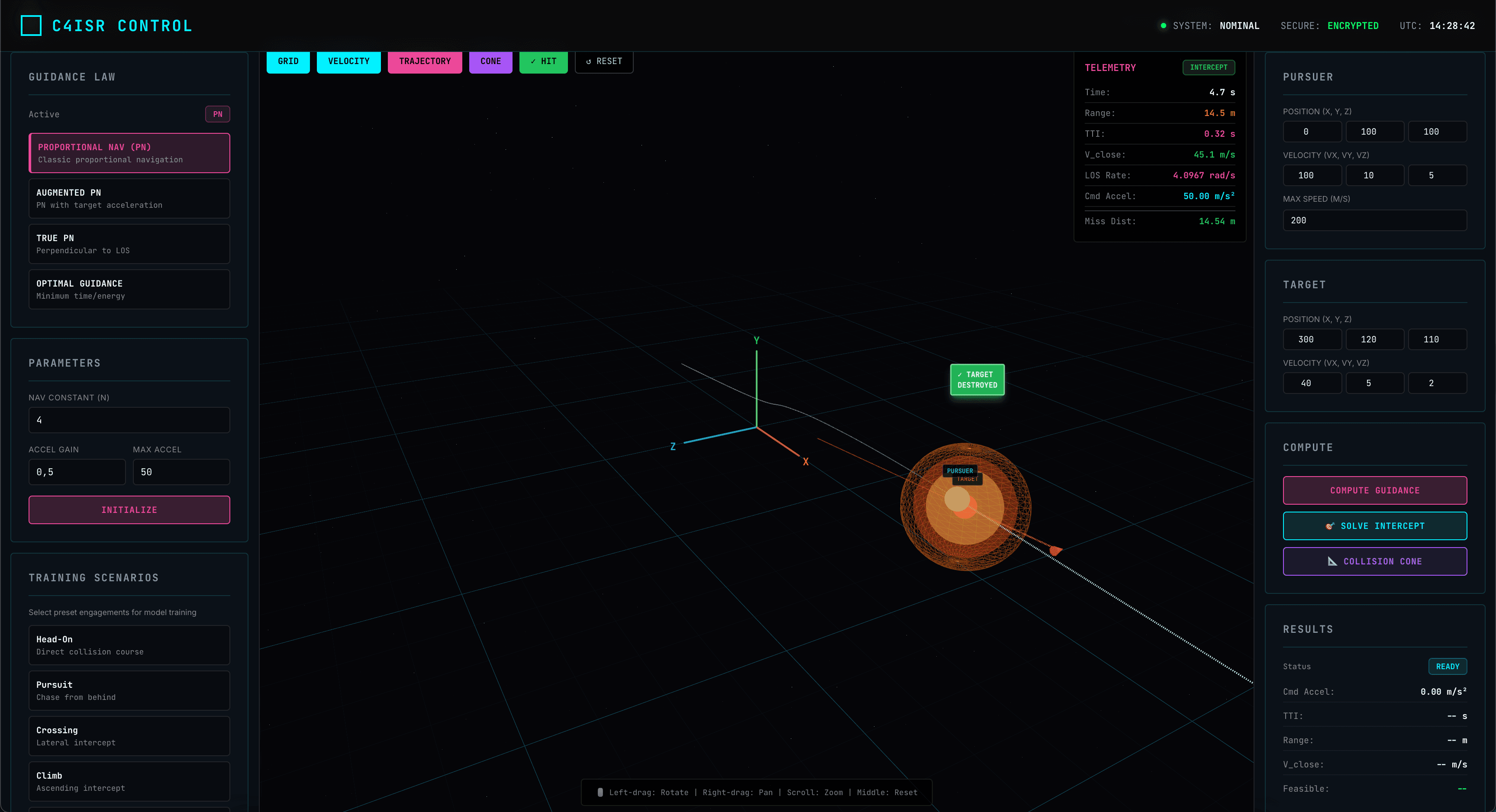
Simulation & Compliance
Digital-twin sandbox for testing missions and strict governance for operational safety.
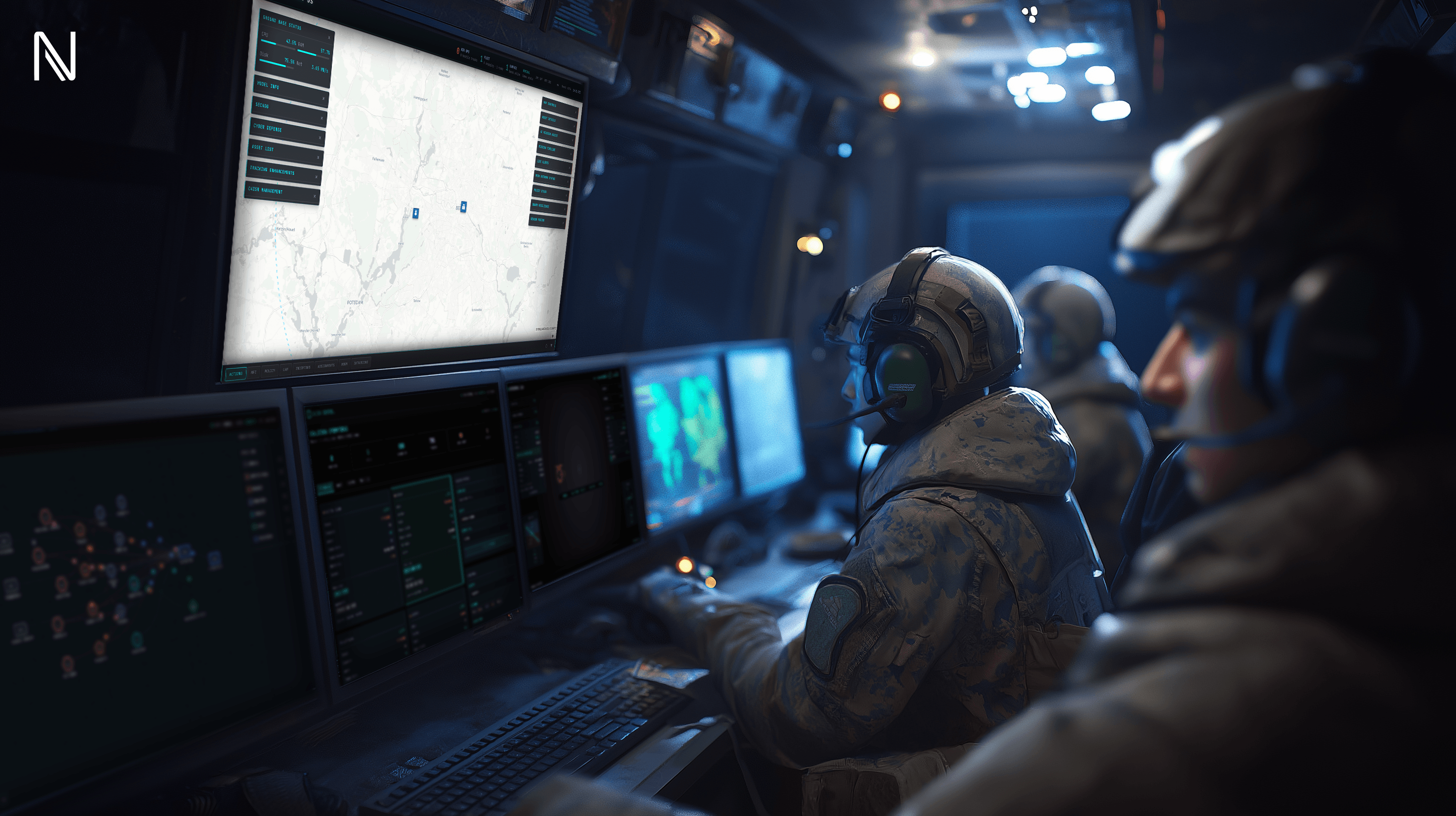
Autonomous systems
that shape the battlespace
in real time
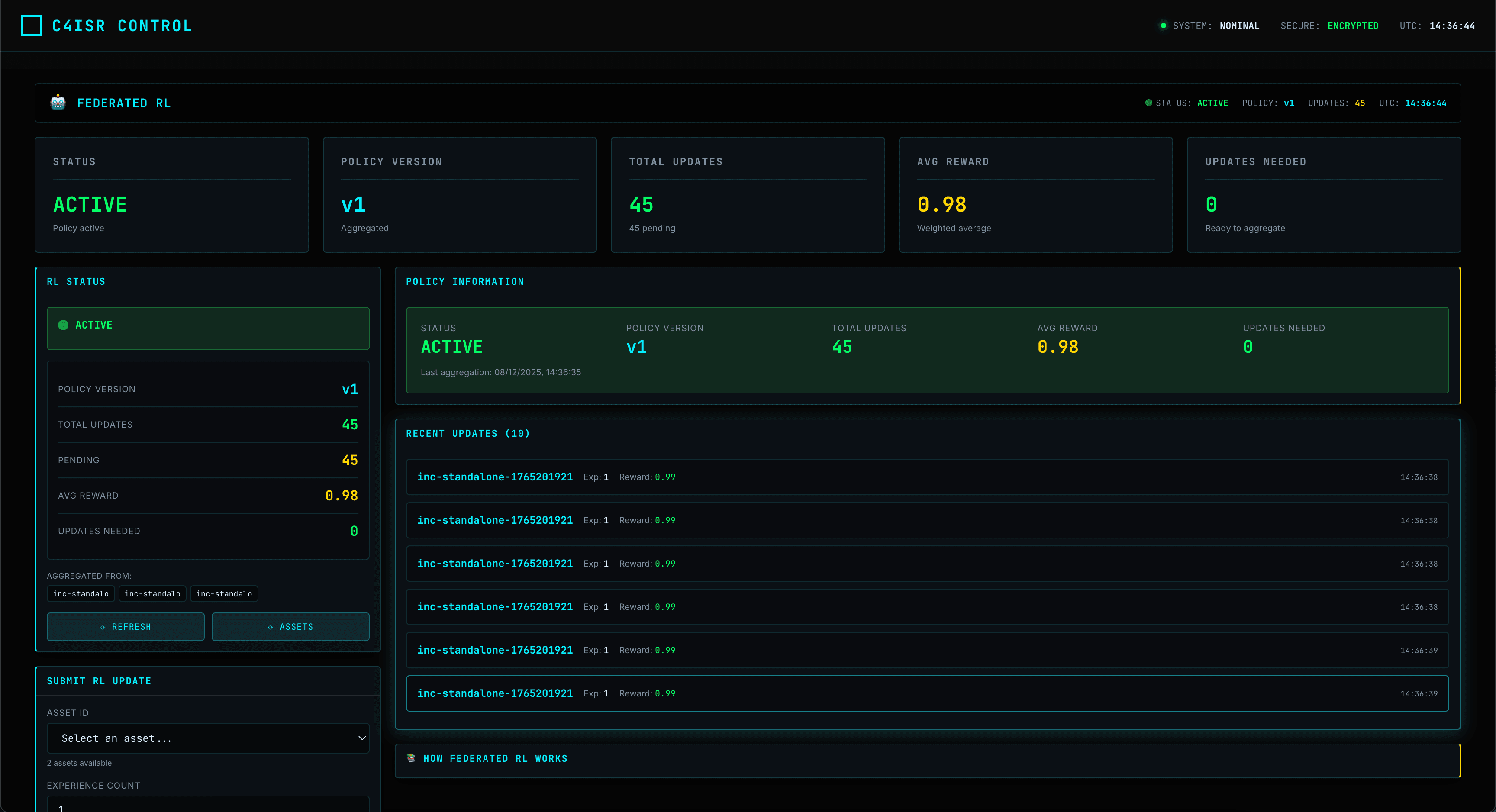
THE SECURE LOOP
Continuous training cycles ensure model improvement without raw data ever leaving the local device.
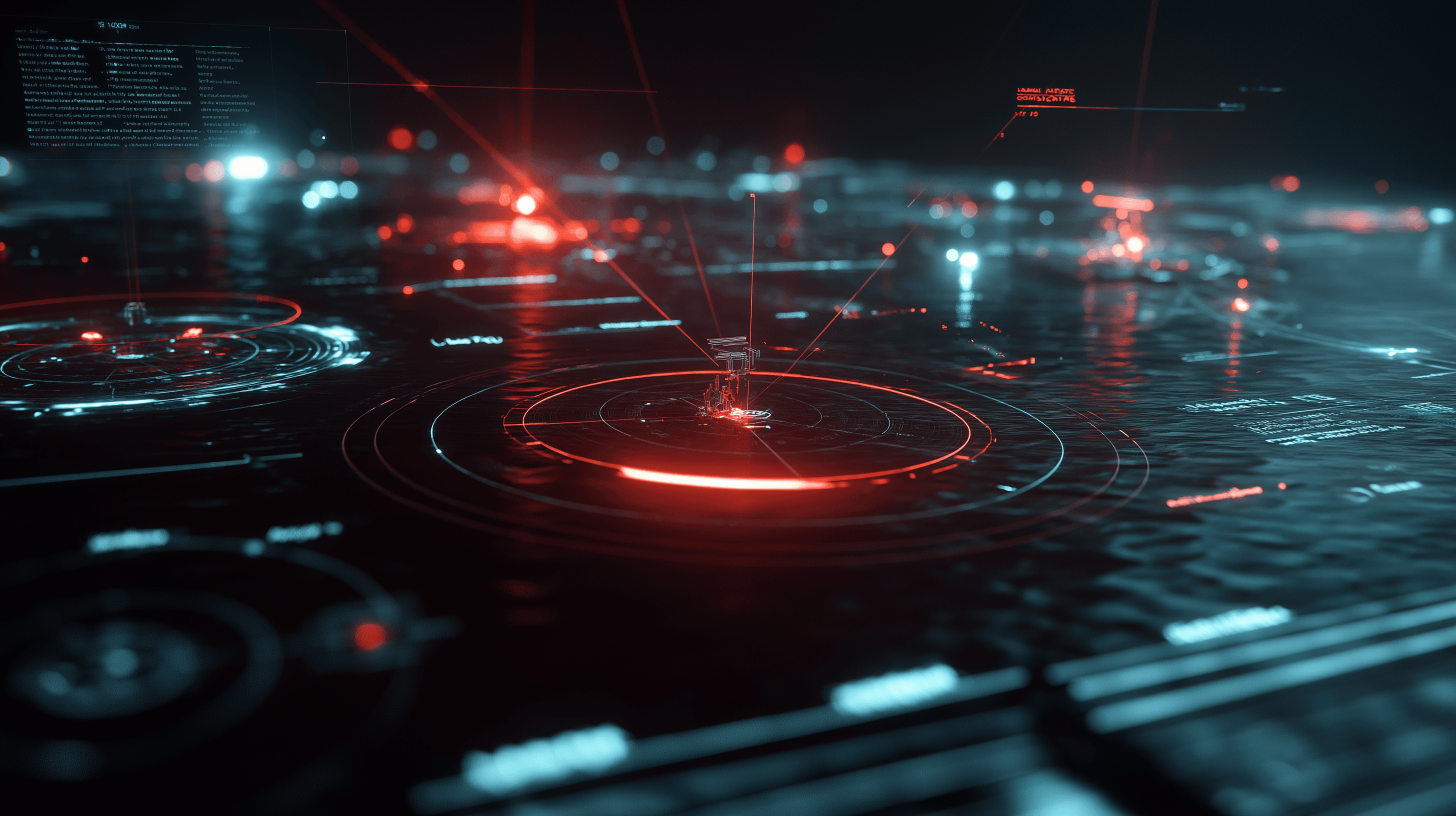
AUTONOMOUS
THREAT NEUTRALIZATION
When a threat is detected, the network isolates the compromised sector immediately. Reinforcement learning algorithms adapt the defense posture across the entire grid in milliseconds.
Sector Alpha
STATUS: OPERATIONAL
Sector Beta
STATUS: THREAT DETECTED - ISOLATING
PULSE VS TRADITION
Strategy
Privacy-first federated learning with MMCP
Traditional centralized or basic federated
Privacy
100% Data Sovereignty & GDPR Native
Partial privacy, data often exported
Cost
90% Reduction vs Hyperscalers
30% Reduction (at best)
Speed
10x Faster via Decentralized Mesh
2x Faster (limited by bandwidth)
FEDSPARSE
OPTIMIZATION
Our proprietary FedSparse technology reduces communication overhead by up to 99% while maintaining model accuracy.
- Sparse Gradient Updates
- Adaptive Compression
- Resilient Aggregation
- Dynamic Bandwidth Allocation
PROVEN METHODOLOGY
Synnq Pulse integrates proven federated learning methods to deliver enterprise-grade performance benchmarks.
GRID CAPABILITIES
Enterprise-grade security infrastructure designed for the most demanding environments.
Zero Trust
Continuous verification of every node and transaction.
Sovereign Cloud
Data residency controls compliant with local laws.
Edge Encryption
Military-grade encryption at rest and in transit.
Anomaly Detection
AI-driven identification of irregular patterns.
Kill Switch
Instant isolation protocols for compromised assets.
Compliance
Built-in adherence to defense regulations.
DEFENSE
INTELLIGENCE
Latest insights, research, and updates on counter-drone intelligence, sovereign threat detection, and federated defense systems.
INITIATE
ENCRYPTED LINK
Deploy the grid. Our defense specialists are ready to architect your sovereign AI infrastructure.
Priority Support
24/7 Dedicated Response Team
Encrypted Channel
End-to-end secure communication